IT Security
SECURE YOUR DATA
The security of your IT infrastructure is a pillar of the successful management of any business or organisation. We offer you comprehensive security solutions to ensure business continuity uninterrupted by unexpected problems or risks.
CYBER SECURITY
RISK ANALYSIS SOFTWARE – SARA
The SARA software solution is a specific tool for risk analysis and evaluation of information assets in accordance with the requirements of Slovak and Czech legislation for cyber security and ISO 27001 standards for the information security management system.
It is intended for people who participate in securing information assets – for cyber security managers, security specialists, asset owners/guarantors, asset managers, risk management experts, auditors.
When registering and evaluating (classifying) assets, it is possible to work in two modes – in detail of a specific asset or by directly and efficiently editing the table with assets in rows and asset attributes in columns.
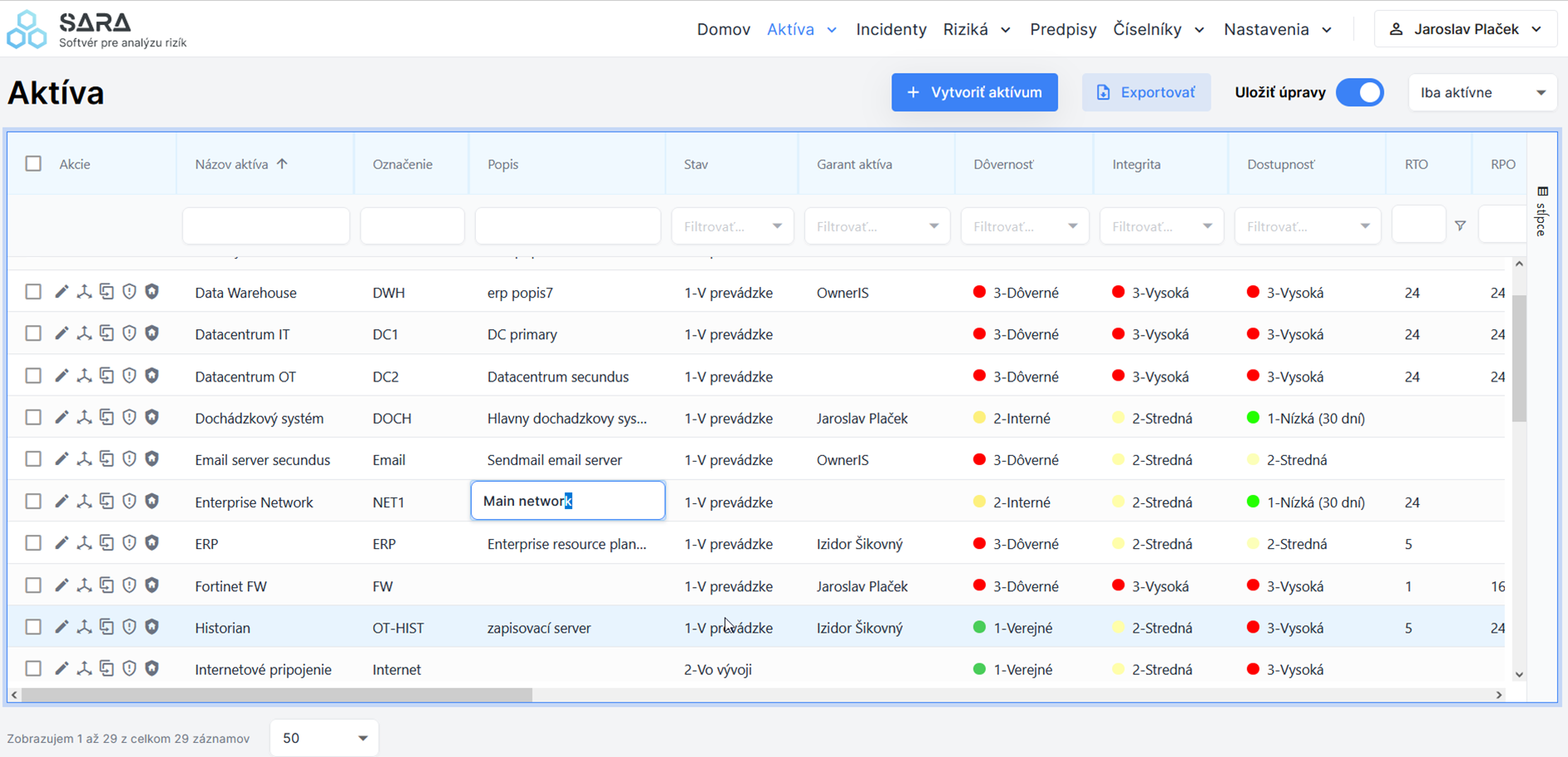
Users can create interlinks between assets, which can be viewed in the visualiser (including the classification level or the identified maximum risk).

Risk assessment is performed by selecting relevant threats for a specific asset, evaluating the likelihood and impact of each threat by a knowledgeable analyst or administrator, and automating the calculation of risk levels and values. For each risk, it is possible to add a detailed scenario, describe the vulnerabilities and counter-measures in place, or link the measures and vulnerabilities to the relevant catalogues and codes. When editing risks, it is possible to use direct editing of values in the table of risks, with the option of bulk editing or copying values at column level.
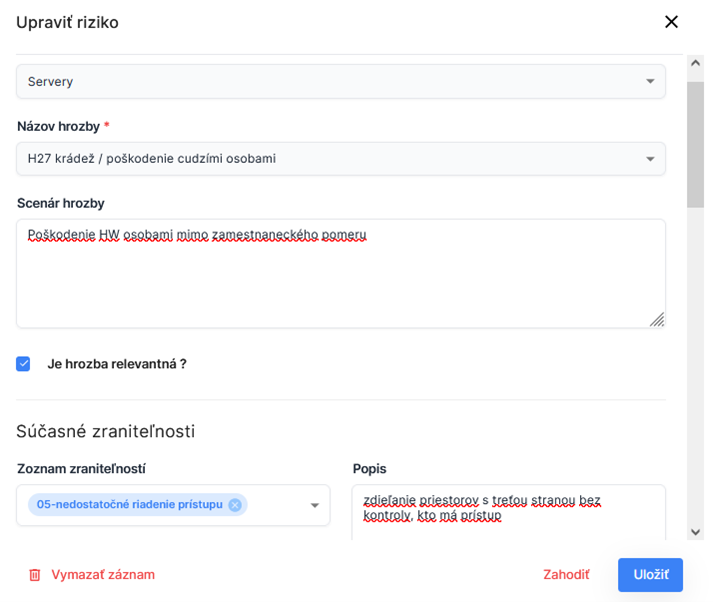
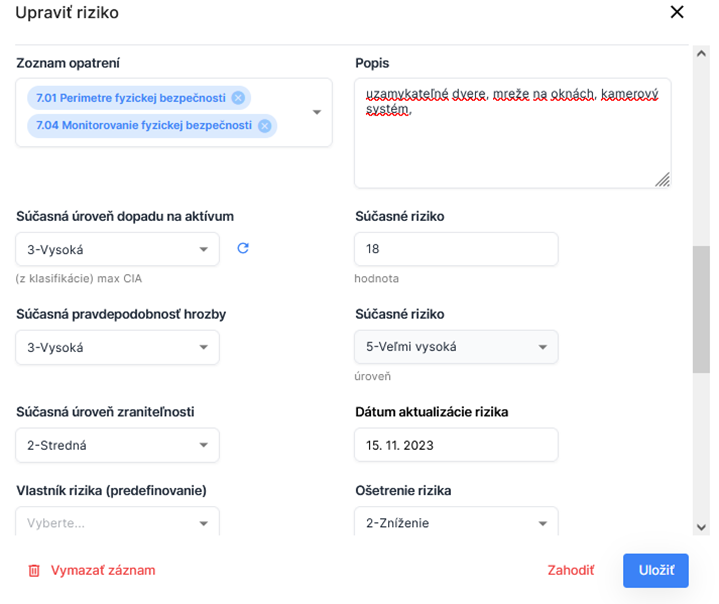
The benefit of this software tool is in its simplicity, intuitive use and transparency. It allows for obtaining a quick overview of the current state of information and cybersecurity within the organisation, with the possibility to use the outputs in cybersecurity audits and review of compliance with legislative requirements.
SARA supports multiple user roles, with applied limitations on the visibility and the extent of permitted data editing.
The architecture of the application is based on the client/server system. The entire solution can be deployed within the customer’s environment or provided externally. The solution also includes support and regular functional and legislative updates.
Summary of Functionality:
- asset recording and valuation, including asset valuation history, with an option for efficient data editing in a spreadsheet style
- risk review and assessment, including risk history, with an option for efficient data editing in a spreadsheet style
- dashboards – overview of cybersecurity status (number of identified risks of different levels, average risk, highest risks), overview of asset classification (expired classifications)
- reports – average risk per asset/total, company risk profile, risk level trend, declaration of applicability of measures (DDA, compliant with ISO 27001)
- registration of cybersecurity regulations (legislation, internal regulations)
- recording of security incidents (link to affected assets, categorisation of incidents according to the Cybersecurity Act, or user-defined; status of incident resolution)
- user roles and permissions – admin, cybersecurity manager, asset owner, asset manager, auditor
- support for binding of SARA user accounts to Active Directory
- customised application for the customer – for asset valuation and risk analysis at the level of base code lists
- user customisation (displaying columns, sorting, filtering …), three language versions (SK, EN, CZ)
You can watch a recording from SARA's presentation at the iDEME 2024 conference here:
IT SECURITY
We offer certified IT security solutions that provide comprehensive security for your data and processes.
Security solutions
- intrusion prevention and detection systems (IPS, IDS and NextGen Firewalls)
- log management and SIEM, analysis of network operations
- backup tools
- DLP
- privileged access management (PAM)
- endpoint detection response (EDR)
Internal audits
-
performance of internal
audits according to ISO 27001 - infrastructure security audits
ISMS according to ISO 27001
- support for the deployment of an information security management system
- risk analysis and management
- preparation of security policies and procedures
- implementation of security tools
- emergency planning and continuity planning
Certified solutions for your security
We provide comprehensive security solutions.
ICS/SCADA
Solutions for industrial organisations to protect against cyber threats
Solutions for industrial organisations to protect against cyber threats
Cybersecurity in organisations does not stopat IT systems and extends into industrial OT (Operations Technology) systems. However, building cybersecurity in OT requires a different approach than IT due to the different requirements of the OT environmentsuch as other priorities, other processes or the impact of cybersecurity on health and safety.
The triad of People – Processes – Technologies is at the core of the cybersecurity system. It is people who are the backbone of cyber security, a fact which is not given enough attention when implementing projects in this area. Cyber security is not a one-time activity, but rather a continuous process that requires continuous improvement and management support. Our services will help you build out and maintain security.
CYBERSECURITY (ISA 62443 & NIST)
- support in deploying an ISA 62443 compliant cybersecurity management system
- risk analysis and management
- preparation of security policies and procedures
- network configuration and security review
- scanning to detect technological vulnerabilities
- design and implementation of a cybersecurity system
- penetration tests
- analysis of the security aspects of device and equipment configuration
- physical inspection of sites and premises
ANY QUESTIONS?
Contact us
Company SYNCHRONIX, a.s. processes your personal data in the scope of the contact form for the purpose of contacting you via the selected communication channel. When processing your personal data for this purpose, we respect and observe your rights when processing personal data. You have the right to object to this processing, and you can do so at any time at the email address privacy@synchronix.sk or on the postal address of the company
WE'LL ADVISE YOU
Together we'll develop solutions



